Phishing Campaign Weaponizes Legitimate LogMeIn RMM for System Persistence
By: Kian |
January 23, 2026 06:00 PM IST |
1 min read
The Rise of "Tool-Based" Backdoors
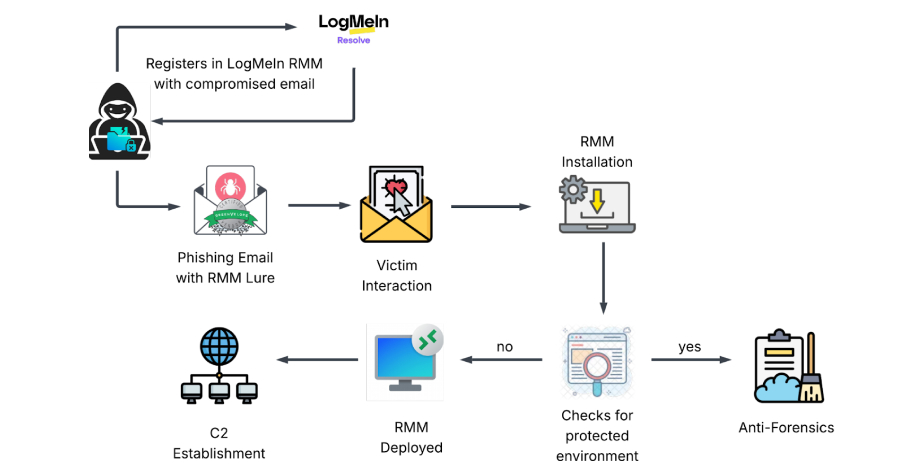
Researchers have uncovered a "Dual-Vector" campaign that uses stolen credentials to deploy LogMeIn (GoTo Resolve)—a legitimate IT management tool—for malicious remote access. Kian Technologies highlights that these attacks are harder to detect because they use "Trusted" software.
The Attack Workflow
- Phase 1: Credential Theft: Phishing emails disguised as "Greenvelope" invitations trick users into logging into fake Outlook or Yahoo pages.
- Phase 2: RMM Deployment: Using stolen credentials, attackers register with LogMeIn and deploy a signed binary,
GreenVelopeCard.exe. - Phase 3: Persistence: The tool is configured to run as a system service with hidden scheduled tasks, ensuring it restarts even if the user terminates it.
Defense Strategies
To counter these "Skeleton Key" attacks, organizations must move beyond simple antivirus. Kian Technologies recommends:
- MFA Implementation: Multi-factor authentication is the only way to stop stolen credentials from being used.
- RMM Monitoring: Use EDR tools to flag any unauthorized installations of LogMeIn, AnyDesk, or ScreenConnect.
- Binary Whitelisting: Restrict the execution of new binaries unless they are pre-approved by the IT department.
Become a Malware Analysis Expert As hackers switch to modern languages like Golang to build evasive tools, the industry needs experts who can deconstruct and stop these threats.
Join the Best Ethical Hacking Institute in Bhilai & Raipur: Learn Malware Analysis, Reverse Engineering, and Advanced Threat Hunting. Enroll now to start your journey in Cybersecurity!



7 Comments
Arjun Saxena (24 Jan 2026, 09:00 AM)
The detail on the AitM attacks is eye-opening. Excellent read.
Rohan Joshi (24 Jan 2026, 06:00 AM)
Impressive breakdown of the TikTok deal. Data sovereignty is the future.
Manish Pandey (24 Jan 2026, 06:00 AM)
Very insightful post! This really helps in understanding modern threats.
Tanuja Mishra (24 Jan 2026, 05:00 AM)
Thanks for the update on these CVEs. Very timely information!
Abhishek Nair (23 Jan 2026, 09:00 PM)
The point about homoglyph attacks (rn vs m) is something everyone should watch out for.
Sneha Reddy (23 Jan 2026, 07:00 PM)
Thanks for the update on these CVEs. Very timely information!
Priya Patel (23 Jan 2026, 06:00 PM)
Great analysis by Kian Technologies. Keeping our systems patched is indeed critical.